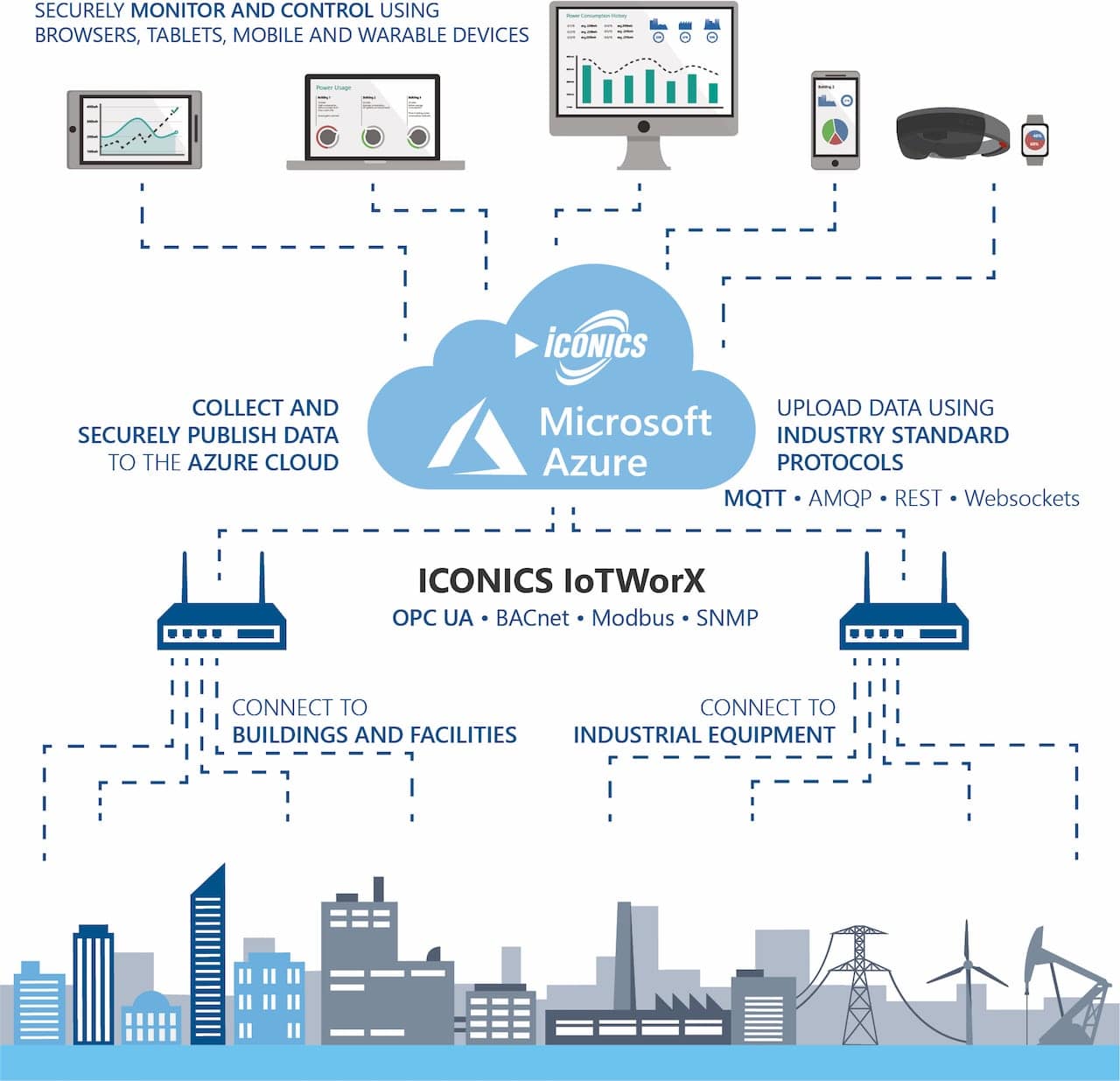
As the Internet of Things (IoT) continues to expand, securely connecting remote IoT devices has become a critical concern for businesses and individuals alike. With the rise in peer-to-peer (P2P) and SH hacker attacks, it is essential to understand the vulnerabilities associated with IoT networks and how to protect them. This article explores the importance of secure IoT connections and provides actionable strategies to safeguard your devices against malicious actors.
The increasing number of connected devices has created a vast attack surface for hackers. From smart homes to industrial automation systems, IoT devices are now an integral part of daily life. However, without proper security measures, these devices can be exploited by P2P hackers and other cybercriminals. In this article, we will delve into the challenges of securing IoT devices and offer practical solutions to mitigate risks.
By the end of this guide, you will have a clear understanding of how to securely connect remote IoT devices while protecting them from P2P SH hacker threats. Let’s explore the intricacies of IoT security and how to implement best practices to safeguard your network.
Read also:The Enigmatic Star Wars Christmas Special An Indepth Exploration
Understanding IoT Security Challenges
The Internet of Things (IoT) brings immense convenience and efficiency to our lives, but it also introduces significant security challenges. One of the primary concerns is the vulnerability of IoT devices to unauthorized access. Hackers often exploit weak security protocols, outdated firmware, and insufficient encryption to gain control of these devices.
Peer-to-peer (P2P) networks, which allow direct communication between devices, can exacerbate these vulnerabilities. P2P SH hackers specifically target IoT devices that lack robust security measures, making it crucial to implement advanced protection mechanisms. Below are some common challenges in IoT security:
- Limited processing power and memory in IoT devices, which restricts the implementation of strong encryption.
- Default passwords and settings that are rarely changed by users, leaving devices exposed to brute-force attacks.
- Absence of standardized security protocols across different IoT devices and platforms.
Key Vulnerabilities in IoT Networks
IoT networks are prone to several vulnerabilities that hackers can exploit. For instance, devices with unpatched firmware can become entry points for malicious actors. Additionally, inadequate data encryption during transmission can lead to data breaches. Below are some key vulnerabilities to watch out for:
- Insecure web interfaces that allow unauthorized access to device settings.
- Insufficient authentication mechanisms, such as two-factor authentication (2FA), which can be easily bypassed.
- Unencrypted communication channels that expose sensitive data to interception.
What is P2P SH Hacking?
P2P SH hacking refers to the unauthorized access of IoT devices through peer-to-peer networks. In a P2P network, devices communicate directly with each other without relying on centralized servers. While this setup offers advantages like reduced latency and improved efficiency, it also creates opportunities for malicious actors to exploit vulnerabilities.
P2P SH hackers often use sophisticated techniques to infiltrate IoT networks. These attacks can result in data theft, device compromise, and even complete network takeover. Understanding the methods used by P2P SH hackers is essential for developing effective countermeasures.
Common Techniques Used by P2P SH Hackers
P2P SH hackers employ various techniques to breach IoT networks. Some of the most common methods include:
Read also:The Comprehensive Guide To Pads With Wings Unraveling Comfort And Convenience
- Man-in-the-Middle (MitM) attacks, where hackers intercept and alter communication between devices.
- Denial-of-Service (DoS) attacks, which overwhelm devices with excessive traffic, rendering them unusable.
- Exploitation of zero-day vulnerabilities in device firmware or software.
Why Securely Connecting Remote IoT Devices Matters
Securely connecting remote IoT devices is vital for protecting sensitive data and maintaining operational integrity. With the proliferation of IoT devices in industries such as healthcare, finance, and manufacturing, the stakes are higher than ever. A single compromised device can lead to widespread network breaches, financial losses, and reputational damage.
Furthermore, secure IoT connections are essential for ensuring compliance with industry regulations and standards. Failure to implement adequate security measures can result in legal consequences and hefty fines. By prioritizing IoT security, organizations can safeguard their assets and maintain trust with customers.
The Impact of P2P SH Hacking on Businesses
P2P SH hacking can have devastating effects on businesses, particularly those that rely heavily on IoT technology. Below are some potential impacts:
- Financial losses due to data breaches and network downtime.
- Damage to brand reputation and customer trust.
- Increased regulatory scrutiny and compliance costs.
Best Practices for Securing IoT Networks
Implementing best practices is crucial for securing IoT networks against P2P SH hackers and other cyber threats. Below are some effective strategies to enhance IoT security:
1. Regular Firmware Updates
Keeping IoT device firmware up to date is one of the most effective ways to mitigate vulnerabilities. Manufacturers frequently release patches to address known security issues, so it is essential to install updates promptly. Additionally, consider enabling automatic updates whenever possible to ensure devices remain protected.
2. Strong Authentication Mechanisms
Implementing strong authentication mechanisms, such as two-factor authentication (2FA), can significantly reduce the risk of unauthorized access. Require users to create unique, complex passwords and avoid using default credentials provided by manufacturers.
3. Encryption of Data in Transit
Encrypting data transmitted between IoT devices ensures that sensitive information remains secure even if intercepted by malicious actors. Use industry-standard encryption protocols, such as TLS, to protect data during transmission.
Building a Secure IoT Infrastructure
Creating a secure IoT infrastructure requires a holistic approach that addresses both hardware and software vulnerabilities. Below are some key steps to consider:
1. Network Segmentation
Segmenting IoT networks can limit the potential damage caused by a successful attack. By isolating critical devices and systems, organizations can prevent attackers from moving laterally across the network.
2. Device Monitoring and Management
Continuous monitoring of IoT devices is essential for detecting and responding to suspicious activity. Use centralized management platforms to track device performance, identify anomalies, and apply security policies consistently.
3. Regular Security Audits
Conducting regular security audits helps identify vulnerabilities before they can be exploited by hackers. Engage third-party security experts to perform thorough assessments and provide recommendations for improvement.
Tools and Technologies for IoT Security
A variety of tools and technologies are available to enhance IoT security. Below are some notable options:
1. Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) monitor network traffic for signs of malicious activity and alert administrators to potential threats. These systems can help detect and respond to P2P SH hacking attempts in real-time.
2. Blockchain Technology
Blockchain technology offers a decentralized approach to securing IoT networks. By leveraging blockchain’s immutable ledger, organizations can ensure the integrity of data and prevent unauthorized modifications.
3. AI-Powered Threat Intelligence
AI-powered threat intelligence platforms use machine learning algorithms to analyze vast amounts of data and identify emerging threats. These tools can help organizations stay ahead of P2P SH hackers by predicting and preventing attacks.
Case Studies: Real-World Examples of IoT Security Breaches
Examining real-world examples of IoT security breaches can provide valuable insights into the tactics used by P2P SH hackers and the importance of robust security measures. Below are two notable cases:
1. Mirai Botnet Attack
The Mirai botnet attack in 2016 highlighted the vulnerabilities of IoT devices. Hackers exploited weak security protocols to compromise thousands of devices, creating a massive botnet that launched large-scale DDoS attacks.
2. Smart Home Device Breach
In another instance, a popular smart home device was compromised due to insufficient authentication mechanisms. Hackers gained access to users’ personal data, including video feeds from security cameras, raising serious privacy concerns.
Future Trends in IoT Security
The field of IoT security is evolving rapidly, with new technologies and strategies emerging to combat emerging threats. Below are some trends to watch:
1. Edge Computing
Edge computing brings processing power closer to the source of data, reducing latency and improving security. By processing data locally, edge computing minimizes the risk of interception during transmission.
2. Quantum Cryptography
Quantum cryptography offers a revolutionary approach to securing IoT networks. By leveraging the principles of quantum mechanics, this technology provides virtually unbreakable encryption for data transmissions.
3. Zero-Trust Architecture
Zero-trust architecture assumes that all devices and users are potentially malicious until proven otherwise. This approach requires continuous verification and authentication, enhancing the security of IoT networks.
Conclusion
Securing remote IoT devices against P2P SH hackers is a critical task in today’s interconnected world. By understanding the challenges, implementing best practices, and leveraging advanced tools and technologies, organizations can protect their networks and maintain trust with customers.
We encourage you to take action by reviewing your current IoT security measures and implementing the strategies outlined in this article. Don’t forget to share your thoughts in the comments section below and explore other articles on our site for more valuable insights into IoT security.
Table of Contents
- Understanding IoT Security Challenges
- What is P2P SH Hacking?
- Why Securely Connecting Remote IoT Devices Matters
- Best Practices for Securing IoT Networks
- Building a Secure IoT Infrastructure
- Tools and Technologies for IoT Security
- Case Studies: Real-World Examples of IoT Security Breaches
- Future Trends in IoT Security
- Conclusion