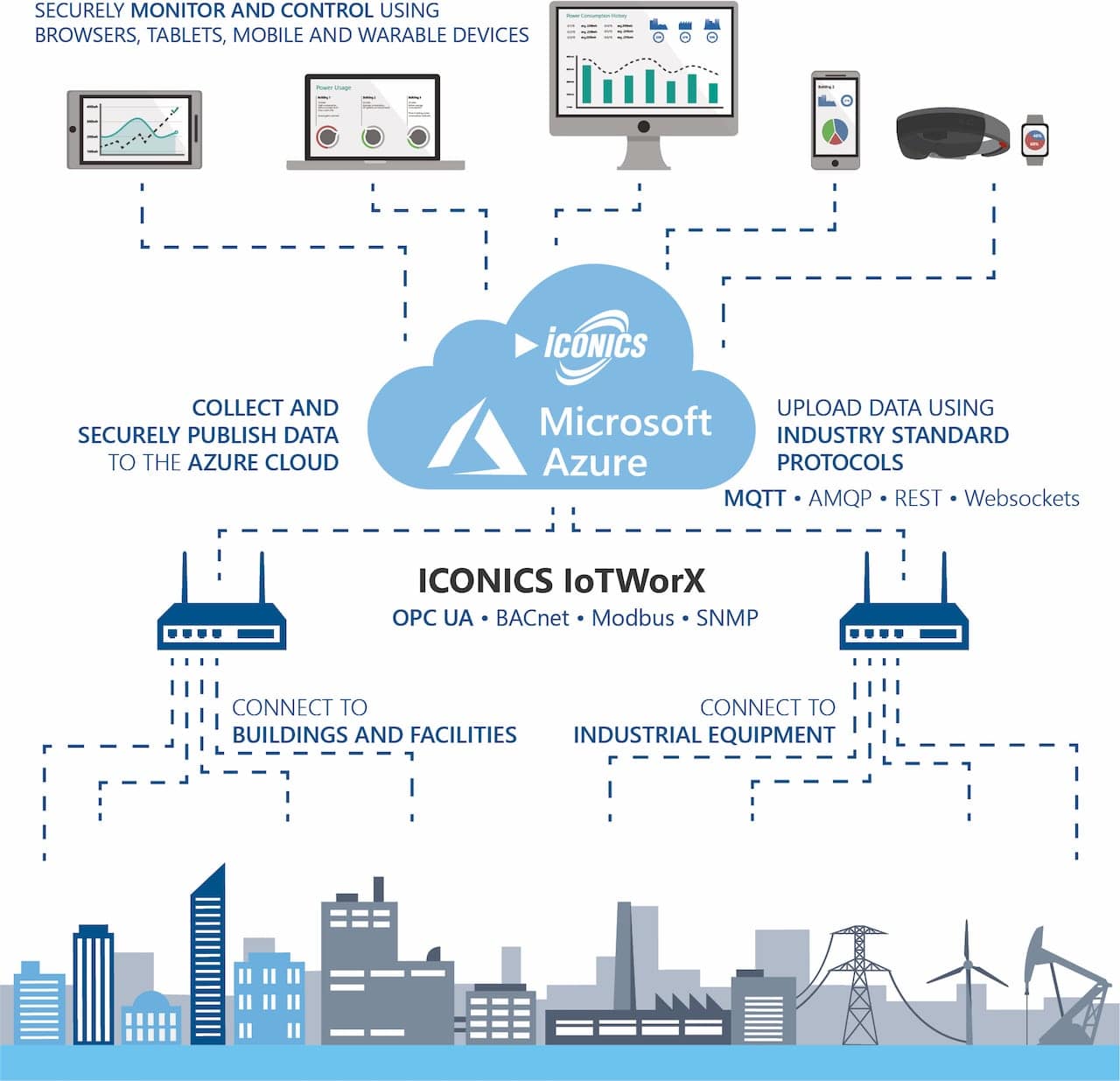
Connecting remote IoT devices using P2Psh on Ubuntu is a critical process that requires careful consideration of security, efficiency, and reliability. As more organizations adopt IoT technology, ensuring secure communication between devices has become paramount. This article provides an in-depth exploration of how to securely connect remote IoT devices using P2Psh on Ubuntu, covering essential configurations, best practices, and troubleshooting tips.
In today's interconnected world, IoT devices are transforming industries by enabling seamless data exchange and automation. However, the security risks associated with these devices cannot be overlooked. This guide aims to equip readers with the knowledge and tools necessary to protect their IoT networks while maximizing performance. Whether you're a developer, system administrator, or IT professional, this article will provide valuable insights into securing your IoT infrastructure.
By the end of this article, you'll understand the importance of secure connections, learn how to configure P2Psh on Ubuntu, and discover strategies to mitigate potential vulnerabilities. Let's dive into the details and ensure your IoT ecosystem remains robust and secure.
Read also:The Fascinating World Of Homie A Comprehensive Exploration
Table of Contents
- Introduction to IoT and P2Psh
- Setting Up Ubuntu for IoT
- Basics of Secure Connections
- Overview of P2Psh
- Installation Process
- Configuration Steps
- Enhancing Security Measures
- Troubleshooting Common Issues
- Best Practices for IoT Security
- Conclusion
Introduction to IoT and P2Psh
The Internet of Things (IoT) represents a network of physical devices embedded with sensors, software, and connectivity, allowing them to exchange data. P2Psh, or Peer-to-Peer Shell, is a powerful tool that facilitates secure remote access to IoT devices. By leveraging P2Psh on Ubuntu, organizations can manage and monitor their IoT ecosystems effectively.
IoT devices often operate in remote locations, making secure connectivity a top priority. P2Psh offers a solution by enabling encrypted communication channels, ensuring data integrity and confidentiality. This subheading explores the fundamentals of IoT and highlights the role of P2Psh in enhancing security.
Why Choose P2Psh for IoT?
P2Psh stands out due to its:
- Efficient peer-to-peer architecture
- Strong encryption protocols
- Compatibility with various operating systems, including Ubuntu
Setting Up Ubuntu for IoT
Ubuntu is a popular Linux distribution favored for its stability and ease of use. Before connecting remote IoT devices using P2Psh, it's essential to set up a robust Ubuntu environment. This section outlines the steps required to prepare your Ubuntu system for IoT deployment.
Key Steps for Ubuntu Setup
Follow these steps to configure your Ubuntu machine:
- Update the system using
sudo apt update && sudo apt upgrade. - Install necessary packages such as OpenSSH and Python.
- Configure firewall settings to allow secure connections.
Basics of Secure Connections
Secure connections form the backbone of any IoT network. Understanding the principles of secure communication is crucial for protecting sensitive data. This section delves into the basics of secure connections, emphasizing encryption, authentication, and authorization.
Read also:Squirrel Repellent Effective Ways To Keep Your Home And Garden Safe
Encryption Protocols
Popular encryption protocols include:
- TLS (Transport Layer Security)
- SSL (Secure Sockets Layer)
- AES (Advanced Encryption Standard)
Overview of P2Psh
P2Psh is a versatile tool designed for secure remote access. It employs peer-to-peer technology to establish direct connections between devices, bypassing traditional server-client architectures. This section provides an overview of P2Psh, highlighting its features and benefits.
Advantages of P2Psh
Some key advantages of P2Psh include:
- Reduced latency
- Improved scalability
- Enhanced security through end-to-end encryption
Installation Process
Installing P2Psh on Ubuntu involves several straightforward steps. This section walks you through the installation process, ensuring a smooth setup experience.
Step-by-Step Installation
- Download the P2Psh package from the official website.
- Extract the package using
tar -xvf p2psh.tar.gz. - Run the installation script with
sudo ./install.sh.
Configuration Steps
Proper configuration is vital for optimizing P2Psh performance. This section outlines the configuration steps required to connect remote IoT devices securely.
Configuring P2Psh
To configure P2Psh:
- Edit the configuration file located at
/etc/p2psh/config. - Specify the target device's IP address and port number.
- Enable encryption by setting the
encryptionparameter totrue.
Enhancing Security Measures
Securing your IoT network requires a multi-layered approach. This section discusses advanced security measures to protect your P2Psh connections.
Implementing Firewalls
Firewalls play a critical role in safeguarding IoT devices. Use tools like UFW (Uncomplicated Firewall) to manage incoming and outgoing traffic effectively.
Regular Updates
Keep your system and P2Psh software up to date to patch vulnerabilities. Regular updates ensure your IoT network remains protected against emerging threats.
Troubleshooting Common Issues
Despite careful planning, issues may arise during P2Psh implementation. This section provides troubleshooting tips to resolve common problems.
Connection Issues
If you encounter connection issues, verify the following:
- Correct IP address and port number
- Firewall settings
- Network connectivity
Best Practices for IoT Security
Adopting best practices is essential for maintaining a secure IoT ecosystem. This section summarizes key practices to enhance IoT security.
Regular Audits
Conduct regular security audits to identify and address potential vulnerabilities. This proactive approach ensures your IoT network remains resilient.
User Education
Educate users about security best practices, such as creating strong passwords and recognizing phishing attempts. Empowering users contributes to a more secure IoT environment.
Conclusion
Securing remote IoT connections using P2Psh on Ubuntu is a critical task that demands attention to detail and adherence to best practices. By following the steps outlined in this guide, you can establish a robust and secure IoT network. Remember to prioritize security, regularly update your systems, and educate users about potential risks.
We encourage readers to share their experiences and insights in the comments section below. Additionally, explore other articles on our website for more information on IoT and cybersecurity. Together, let's build a safer digital future!